Phases of an Effective Incident Response Plan
Last Updated March 7, 2024
Despite the precautions businesses and other organizations take to prevent falling victim to cybercrime, many still do.
When it comes to security breaches, “most companies are approaching the problem as not if, but when,” said Jayme Lara, CISSP, MS, IS, an adjunct faculty member in Villanova University’s Certificate in Cybersecurity program.
Lara said it’s vital for businesses to have an effective incident response plan in place. The incident response plan is a process designed to stop the unwanted action, mitigate its impact and begin the process of recovery, according to Robert Arakelian, Assistant Professor of the Practice for Accounting & Information Systems at Villanova.
Arakelian discussed the topics of incident response and disaster recovery in the Essentials of Cybersecurity course, a requirement of the Certificate in Cybersecurity program.
Putting the Incident Response Plan in Place
In cybersecurity terms, an incident is “an attack against an information asset that threatens confidentiality, integrity or the availability of information resources,” said Arakelian.
“An incident response plan works to ensure that a breach is resolved as quickly as possible and with the minimal effect to an organization,” Lara added. “Historically, it is a formal step-by-step process, identifying roles and responsibilities of teams across the organization.”
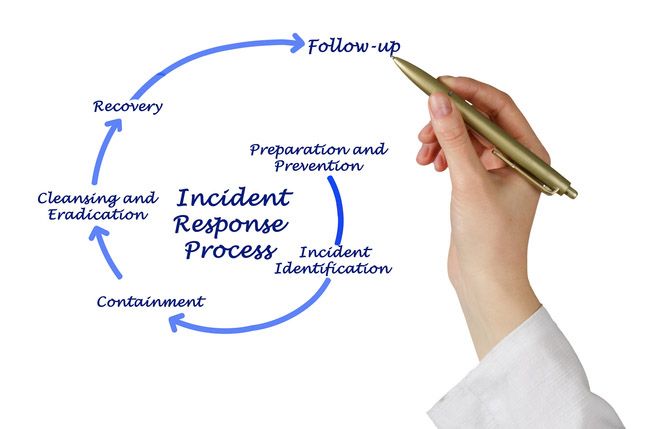
The first phase of an incident response plan is preparation. The plan must be organized so its instructions can be quickly and easily implemented. It must be protected and stored as sensitive information but accessible for those who need it.
The plan needs to be in place and have been thoroughly tested before any suspicious activity occurs. “An untested plan is not useful,” Arakelian said. He called periodic updates and walkthroughs “critical.”
The second phase is identification or detection of a possible breach. This most commonly occurs, Arakelian said, when technical support is requested from the help desk. Cybersecurity professionals look for signs that the incident is hostile. Indications of a possible attack include the presence of unfamiliar files and unusual system crashes.
The presence of new accounts indicates the attack probably should be classified as an incident, while the use of dormant accounts and changes to logs tells trained observers that they conclusively have an incident on their hands.
Cybersecurity professionals must be aware of any possible signs of meddling. The earlier an attack is detected, the sooner the organization can begin battling it.
The third phase of an incident response plan is containment, which involves efforts to prevent more damage from occurring. This phase includes actions that must occur quickly in order to address the issue: alerting key personnel, assigning tasks and documenting the incident. Team members first must re-secure the system and search for and repair any vulnerabilities, as one of these may have been exploited for the breach.
Documentation is essential and cannot be treated as an afterthought. A cybersecurity incident exposes not only the organization’s vital information but also that of its clients and customers. The organization must be able to show that it did everything it could to contain the damage caused by the incident.
Incident Recovery Tips
Once tasks are assigned, the fourth phase, eradication, can begin. Team members should be searching for and removing data affected by the incident. Search engines must be contacted so that bogus information posted during the incident is not archived. They also must ensure that any personal information posted during the incident is removed.
The final two phases of an incident response plan are recovery and lessons learned. Arakelian recommended the following steps for the incident recovery process:
- Identify and resolve vulnerabilities
- Address and replace failed safeguards
- Evaluate and upgrade monitoring capabilities
- Restore data from backups
- Restore necessary systems, processes and services
- Continuously monitor the system
- Restore the organization’s confidence
- Conduct “after-action” review
Studying the operation’s system logs, intrusion detection logs, configuration logs and documents, incident response documentation and systems, and data storage assessment results ideally reveals where and how the system was breached.
Disaster Management Roles
If the damage of an attack or incident can’t be contained, it can become a disaster. According to Arakelian, an incident becomes a disaster when the organization cannot mitigate the impact of the incident while it is occurring, or if the damage or destruction is so severe that the organization cannot recover quickly.
The crisis management team goes into action here. This team’s duties include:
- Managing the event from an enterprise perspective
- Supporting personnel and families during the crisis
- Determining the impact on normal business operations
- Informing customers, suppliers, partners, regulatory agencies, industry organizations and the media about the breach and the organization’s efforts to deal with it.
Being up front with those whose information may have been compromised is essential. Being the victim of a successful cyberattack does little good for an organization’s reputation. A lack of openness about the incident can cause even more damage.
For example, retailer Target suffered a holiday-season data breach in 2013 that affected tens or millions of its customers. The company chose not to announce the breach to the public, Lara said. A blogger broke the news.
“Target should have been the first to announce it, as part of its incident response plan,” Lara said. “The company took a huge hit to its reputation. Knowing the proper incident response is huge.”
Prevention and Recovery
Prevention is job one for an organization’s cybersecurity teams. “Companies need to practice defense-in-depth with multiple advanced technological solutions including encryption, intrusion detection, log management, vulnerability scanning, firewalls and more, in addition to trained cybersecurity professionals experienced in tool usage and implementation,” Lara said.
Even so, organizations need to recognize the likelihood of an attack and have a plan in place to deal with these intrusions, whether large or small.
Verizon’s 2019 Data Breach Investigations Report stated that 43% of data breaches involved small business victims. “No organization is too large or too small to fall victim to a data breach,” according to the report. “Having a sound understanding of the threats you and your peer organizations face, how they have evolved over time, and which tactics are most likely to be utilized can prepare you to manage these risks more effectively and efficiently.”




